There is no easy way to obfuscate Java classes of an Android app. This is no Eclipse plugin, nor even a working ant script.
Maybe there are working ant scripts. But for Android SDK 1.5, it seems like no one has supplied a proper one, yet. And hence, I spent half a day hacking out a script that works. There are more effort and hurdles than what are presented here.. but for a simple working script, here it is how I did it:
1 Create a Project
From the Terminal, in /android-sdk/tools/, run:
./android create project –target 2 –path /PATH/TO/ObfuscatedApp –activity MyActivity –package com.just2me.obfapp
2 Edit build.xml
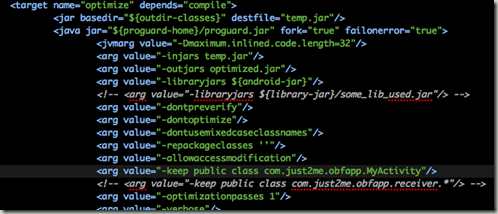
Replace the build.xml with my modified build.xml, which is the most important item in this tutorial. The obfuscation work is in the optimize target as seen below.
Some points to note in the build.xml ant script:
- Edit the properties for the path to your Android SDK and Proguard
- If you use any libraries, copy them to /lib and add -libraryjars ${library-jar}/some_lib_used.jar accordingly
- -dontoptimize is needed for Android
- For all classes that are declared in AndroidManifest.xml Application nodes (Activities, Receviers, etc), add an arg to tell proguard not to obfuscate. Exampe: “-keep public class com.just2me.obfapp.activity.*”
3 Run ant
The last step is to simply run the ant script!
To package a debug version that is signed with a debug key, run “ant debug-obf”.
To package a release version that is unsigned, run “ant release-obf”.
If all is well, then you will find the products in /bin. ObfuscatedApp-debug.apk would be the debug package that could be installed on simulator/devices.